EXCEEDGRC™
Stop using spreadsheets, documents and/or collaboration portals, incident management system, as well as email threads and individual calendars to manage your GRC initiatives. This is inefficient, error prone, costly, and a risk by itself.
GRC activities are primarily a matter of “people and processes” and tools come second. Our EXCEEDGRC™ has a simple, user-friendly interface, easy to understand workflows, a short learning curve, and will be fully functional in a matter of days. EXCEEDGRC™ was developed to save you the maximum amount of time getting your tasks done.
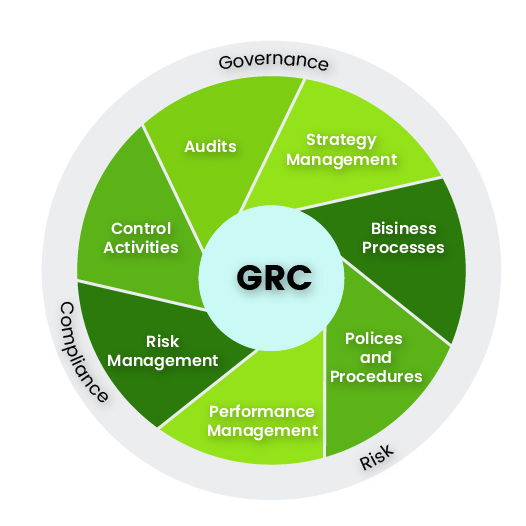
By connecting the Policy to Risk Management and getting the feedback from the Compliance module, this will help organization better:
Governance Management:
Build the right policies and processes in the organization that adheres to the selected standards.
Risk Management:
Understand and evaluate value of Risks associated with operational activities.
Compliance Management:
Determine the level of compliance by determining the level of compliance and Gaps from implementing the desired controls.
The ExceedGRC™ platform is offered in comprehensive package to meet the needs of all organizations.